Services
Penetration Testing
VULNERABILITY ASSESSMENT
Forensic Analysis
Reverse Engineering
Malware Analysis
Cyber Security Readiness Assessment
Powered By
People
Qualified & Experienced Professionals
Process
Governance Risk and Compliance
Technology
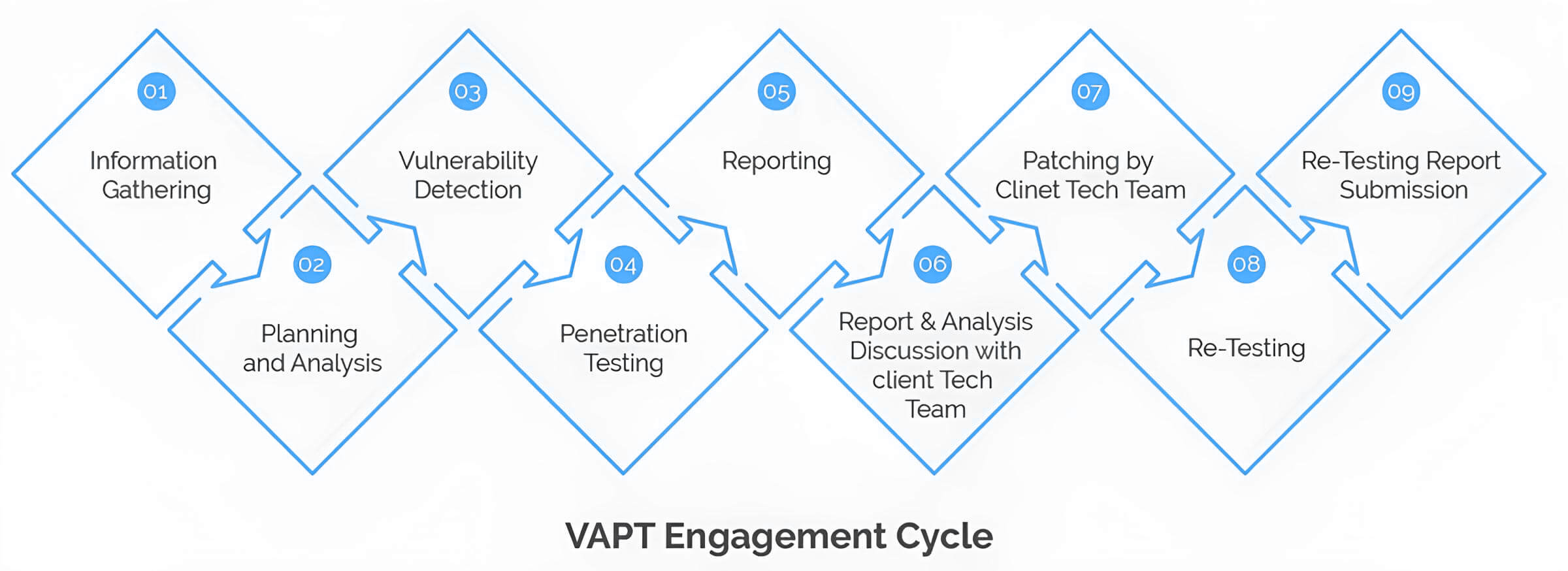
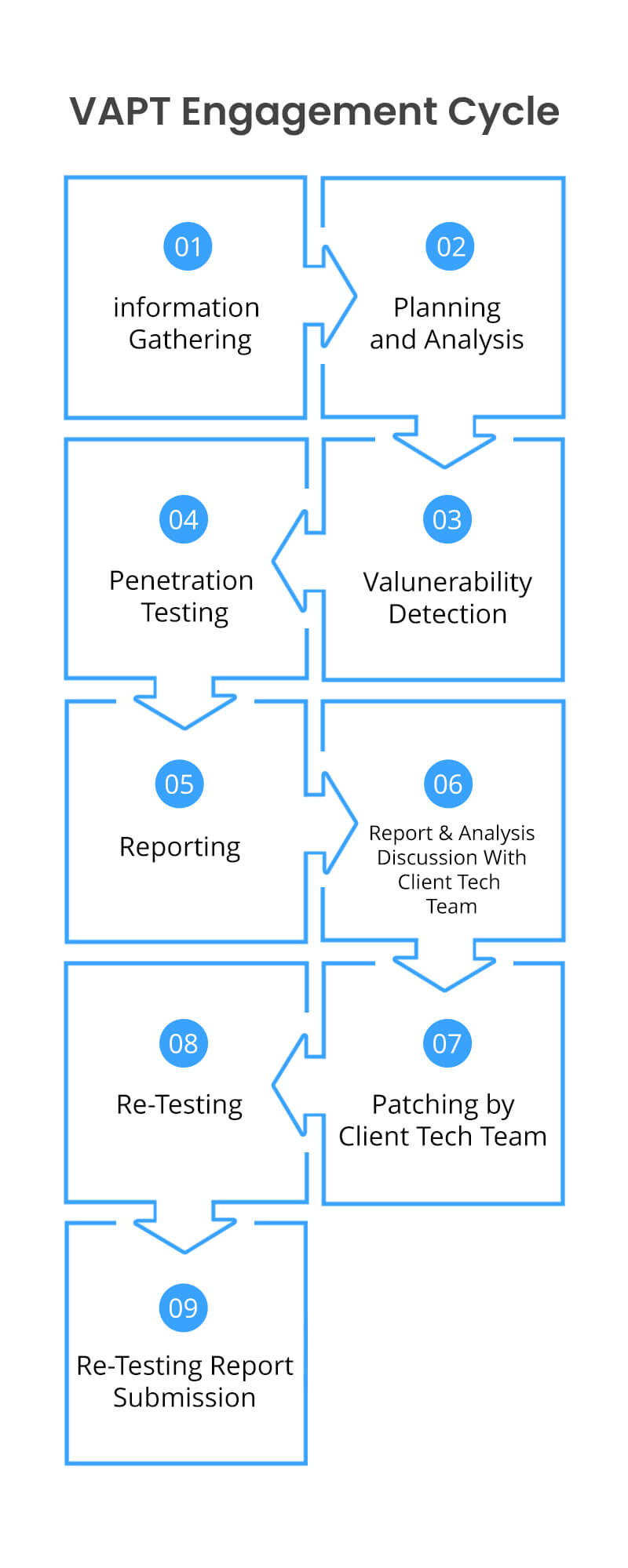
Vulnerability Assessment and Penetration Testing
Top Industry Talent
Our testers have subject matter expertise acquired through years of experience which allows us to have a well-rounded approach.
Meet Our Expert Penetration Testing Team
Securing Business
SOC 2
Prevent data abuse
Securely manage customers’ data
Prevent unauthorized access to the system
Observe a decrease in data breaches
ISO 27001
Protect information assets
Retain your customer base
Secure your brand reputation
Avoid penalties and financial losses
HIPAA
Secure your customers’ PHI
Avoid financial penalties
Prevent public exposure of PHI
Avoid disciplinary action
PCI DSS
Safeguard business
Ensure prioritizing security
Avoid financial penalties & negative PR
Secure your customers’ payment card data
Securing Technology
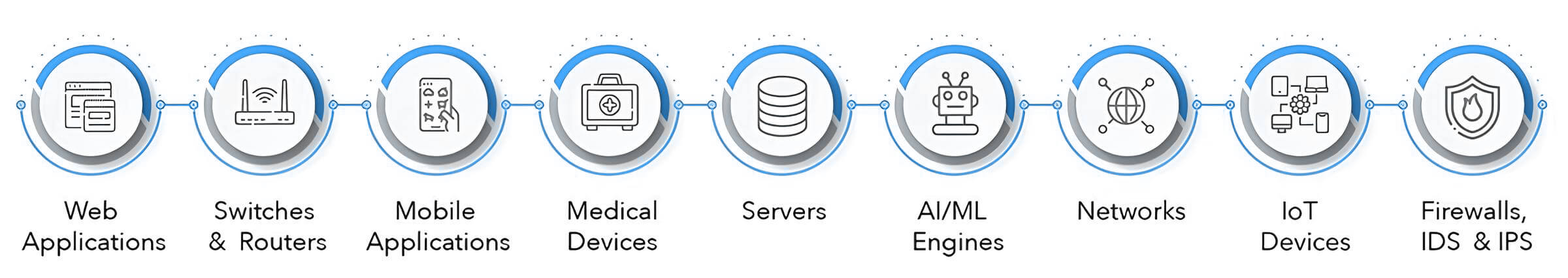
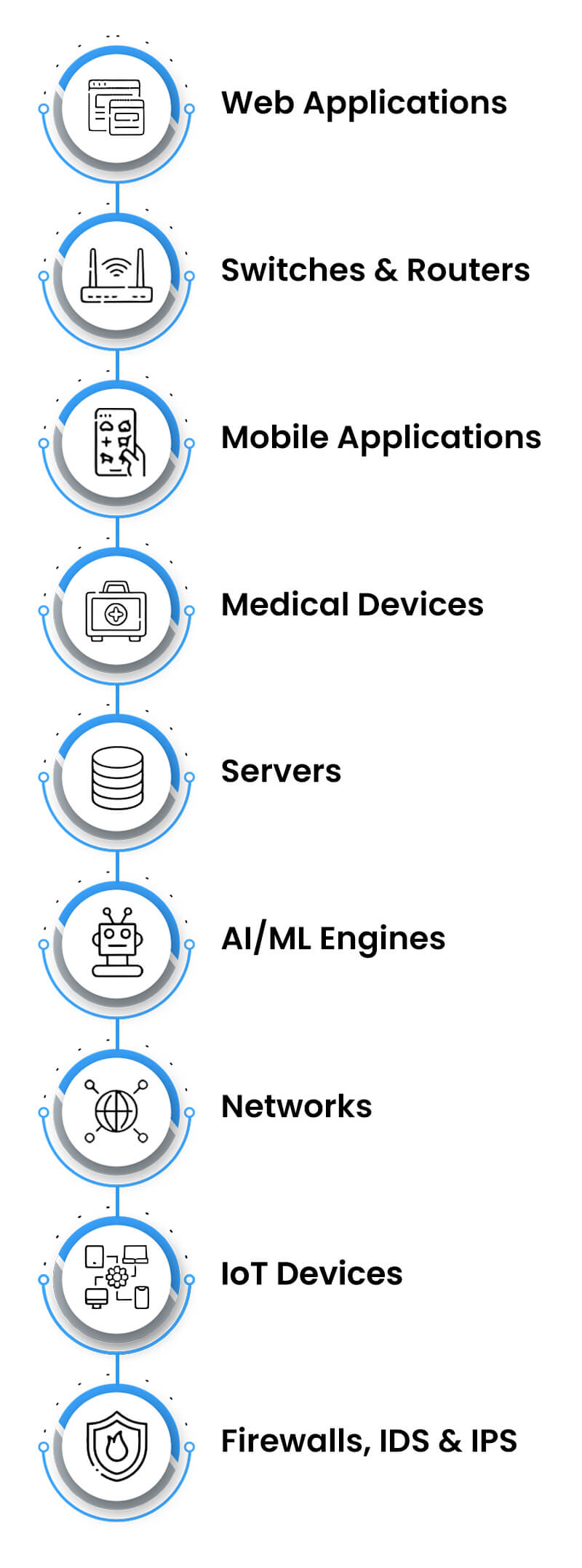
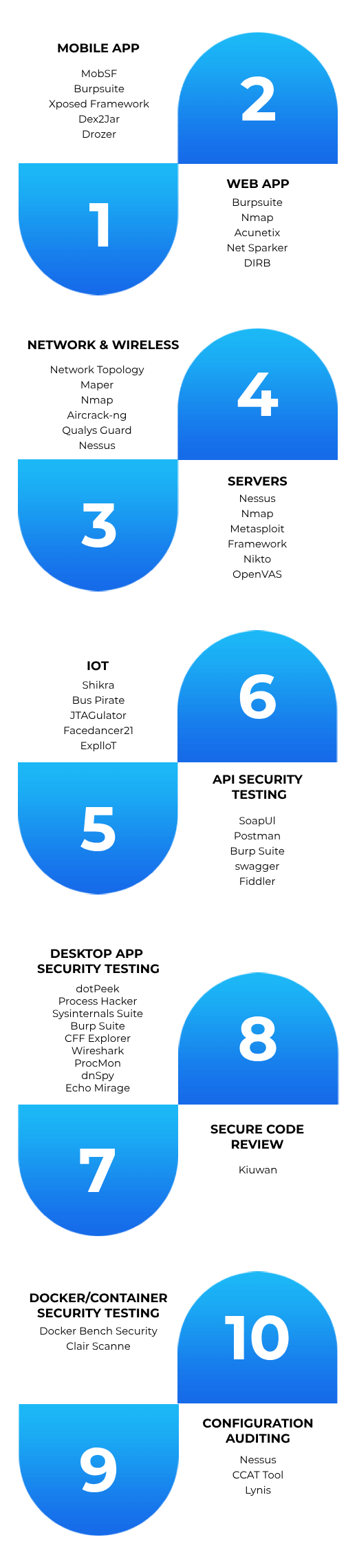
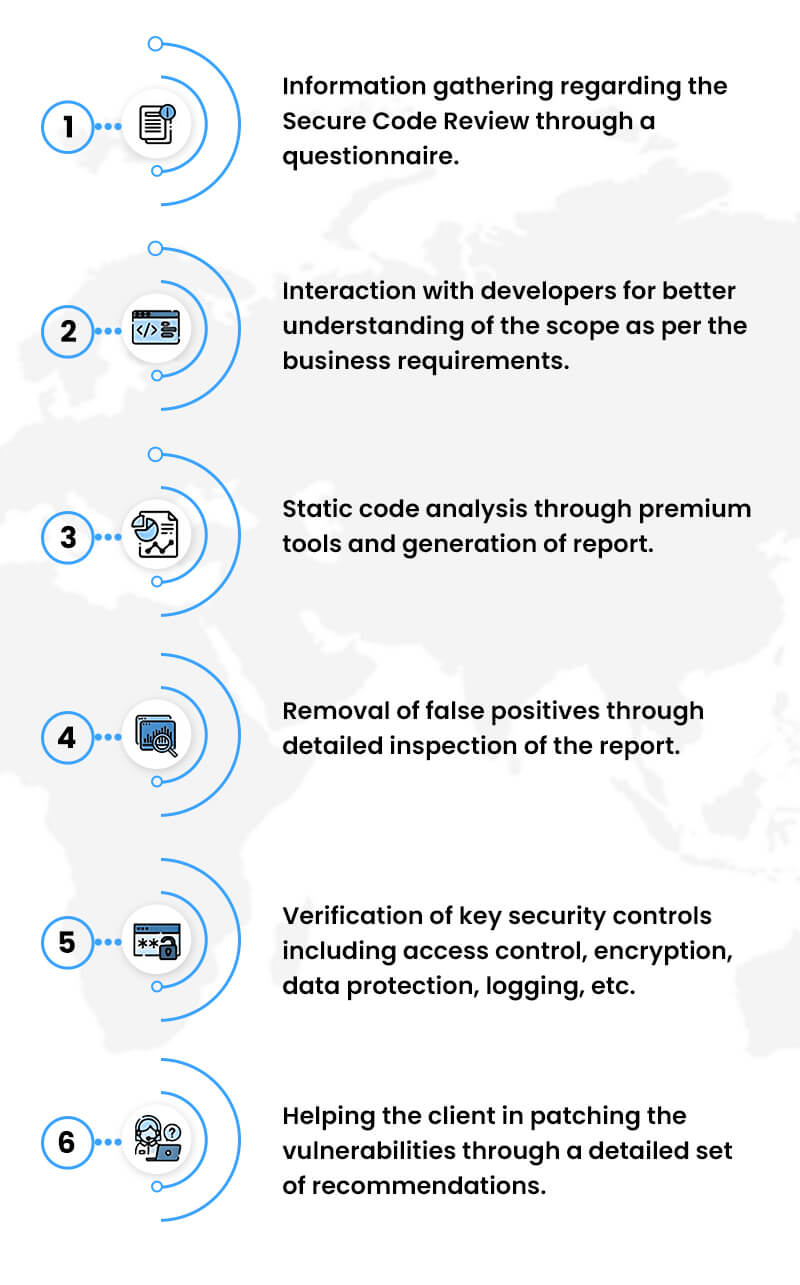
Under our Penetration Testing service, we test the complete IT infrastructure (Mobile/Web App, Servers, Networks, Desktops/Laptops, APIs, CRM/ERP) of an organization. We recommend solutions against all the vulnerabilities and do re-testing after the organization’s engineering team patches all those vulnerabilities.
Reverse-engineering is the act of dismantling an object tp see how it works.
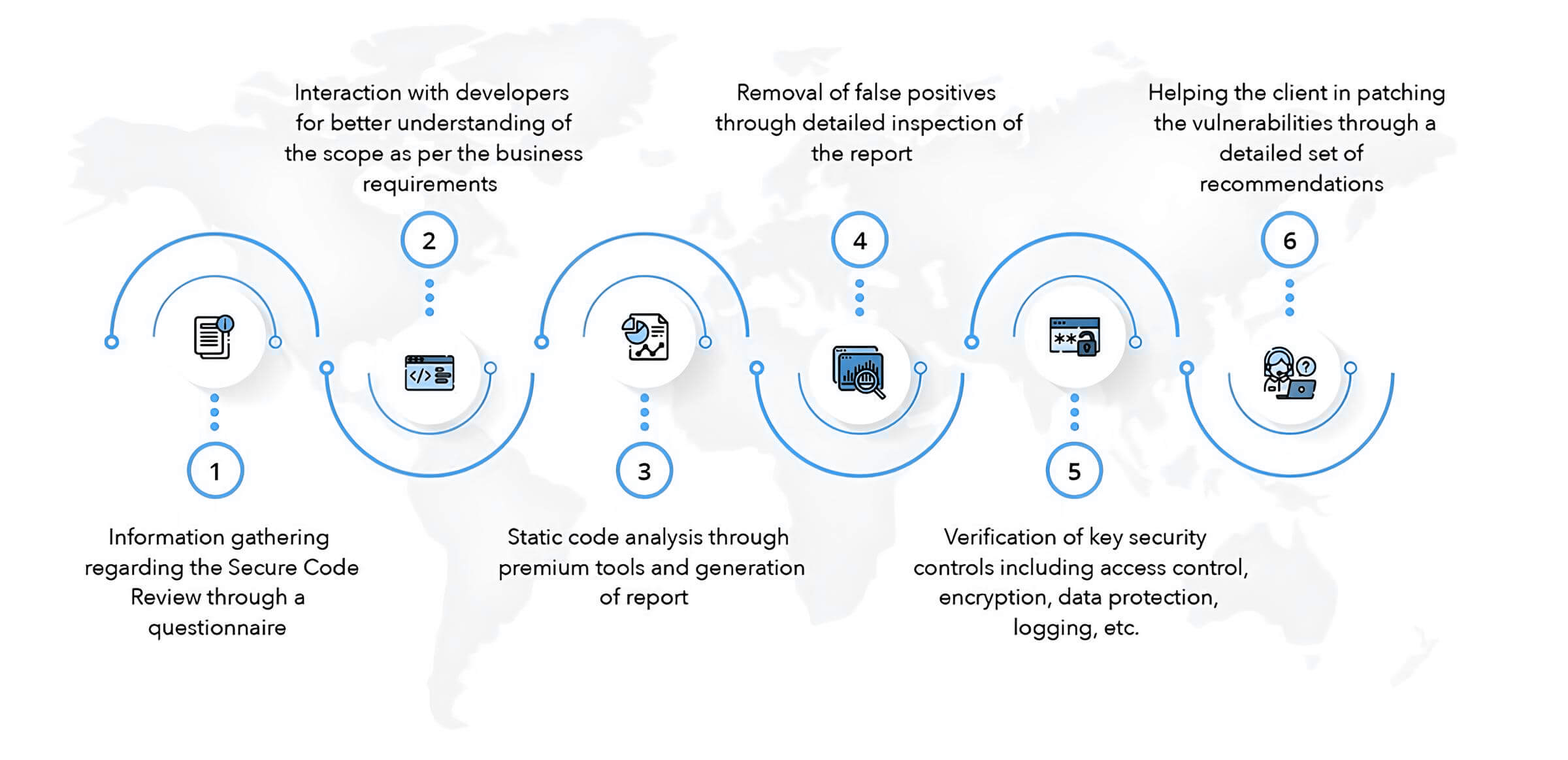
Our experts translate complex analytical findfigs into targeted deliverables for executive, legal, and technical stakeholders to provide insight into the nature and scope of any code-related event.
Through a tailored application of static and dynamic analysis, SafeHak Lab cber experts examine files to enumerate malicious functionality and develop comprehensive tear-down reports.